Recently, I made an appearance on radio station 89.7FM, in the segment called Living, Laughing and Learning with Lisa and JR.
Working in IT, we find that Cyber Security isn’t given the importance that it really does require. Anti-virus is only one small part of staying secure online, but often it’s the only part that people put in place. In my interview with Lisa and JR, we discussed computer threats.
Interview Audio
You can listen to Part 1, the introduction of Cam Rule, here;
[blox_audio title=”Part 1″ image=””]https://support.dt-a.com.au/wp-content/uploads/2018/02/170815_11_Camron-Rule_P1.mp3[/blox_audio]
Part 2 is where we discussed cyber threats, you can have a listen here;
[blox_audio title=”Part 2″ image=””]https://support.dt-a.com.au/wp-content/uploads/2018/02/170815_11_Camron-Rule_P2.mp3[/blox_audio]
Following on from the interview, I have expanded on the most common threats out there, and also suggested some ways to ensure that you’re safe, and able to recover quickly from any kind of infection.
Types of Threats
These days, the list of types of cyber threats is growing. The threat can consist of one or more of these threats;
- Advanced Persistent Threats
- Phishing
- Trojans
- Botnets
- Ransomware
- Distributed Denial of Service (DDoS)
- Wiper Attacks
- Intellectual Property Theft
- Theft of Money
- Cryptolocker
- Spyware/Malware
- Man in the Middle (MITM)
- Drive-By Downloads
- Malvertising/Adware
- Rogue Software
- Unpatched Software
The common ones we see are Phishing, Trojans, Ransomware/Cryptolocker, Spyware/Malware, Malvertising/Adware and Unpatched Software.
Trojans
Trojans are the most common attack type. A Trojan is a type of malware that is usually masquerading as legitimate software. Users are usually tricked by some form of social engineering into loading and executing Trojans on their systems. Once triggered, Trojans are used by criminals to spy on you, steal your confidential data, and gain backdoor access to your infrastructure. With around 800,000 new threats released every day, you’ll need to make sure you have an anti-virus that is kept up to date.
Free anti-viruses don’t provide the best protection, they’re usually not up to date, and often have annoying pop-ups about upgrading and paying for the service. The best anti-viruses are subscription based, and Bitdefender is currently one of the best in class. We use this anti-virus for our managed clients, and certainly recommend it if anyone is looking for a new anti-virus.
The other way viruses commonly get in is through email. Anti-virus can scan and stop some viruses, so the people designing them have gotten smarter. They are sending emails and viruses that can slip past any anti-virus, meaning your staff are the next line of defense.
Ransomware/Cryptolocker
This type of infection can be one of the more serious and scary ones. For a business, if one PC gets infected, it can spread to the server and every other PC on the network. The name Ransomware and Cryptolocker comes from the fact that the infection will encrypt your data, and then you’ll usually get a ransom message to decrypt the data for money. They don’t always decrypt the data however, and often request to be paid in BitCoin or other untraceable currencies.
These types of infections are typically delivered via emails with either links to external websites, or attachments that run the install when opened. A mail filter may help with detecting and stopping some of the emails, however staff training is always the first thing to do upon hiring.
These encryptions are nigh-impossible to crack without the key. The best way to beat a Ransomware virus is with good backups, and a disaster recovery plan.
Staff Training
Staff are the biggest asset any company can have, but they’re also human. Humans can make mistakes, but by providing staff with training they’ll be less likely to make a mistake that could cost you a lot in lost time and productivity.
Virus makers are sending emails that look like legitimate emails, very convincing emails. There are a few small ways to check whether they are legitimate, and it’s always best that if you are unsure, don’t click anything!
The first things to check are the from email, and where the links in the email will take you.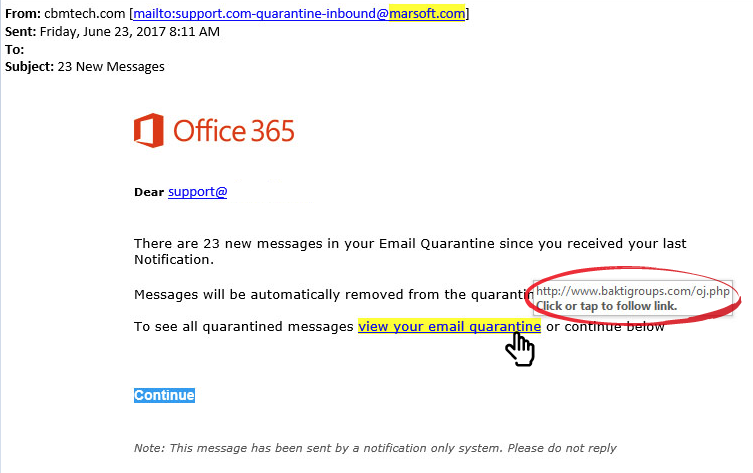 As you can see in the above example, the from email ends in “marsoft.com”. To check the links, hover your mouse over it without clicking until the above preview window appears. If it doesn’t point to where you think it should, do not click it.
As you can see in the above example, the from email ends in “marsoft.com”. To check the links, hover your mouse over it without clicking until the above preview window appears. If it doesn’t point to where you think it should, do not click it.
Even training this simple could stop your staff from getting infected.
For more information on security, read my recent post on 3 tips for stronger security.
Speak to Rule Technology today about training your staff, setting up a disaster recovery plan, and ensuring your backups are set up and working as they should.





